Hey, i bashed my site into 'ZeroDayScan' and even though the report seems incomplete, it did tell me that i have a security risk.
For the purpose of learning how to fix it i will post the error:
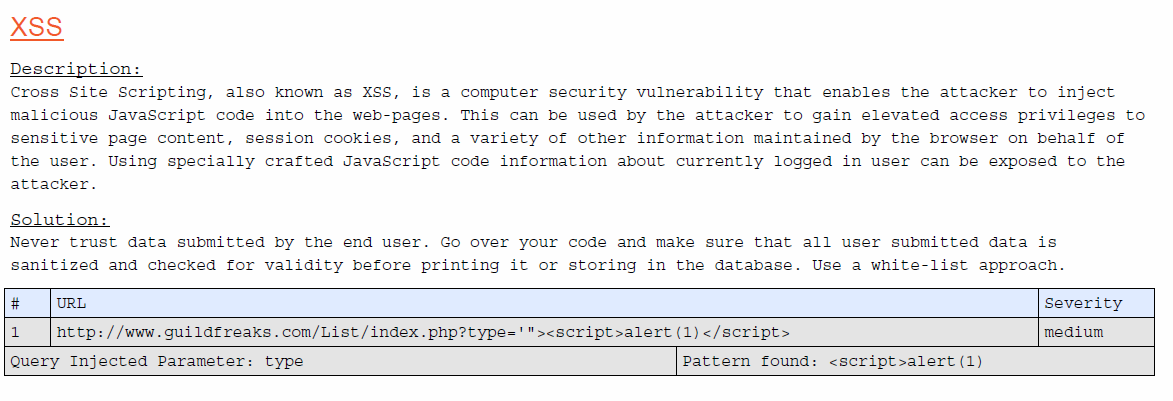
"http://www.guildfreaks.com/List/index.php?type='"><script>alert(1)</script>"
Now all that does anyway is get info from the database, and other than mysql injection (which shouldnt be possible), i dont see how it really is a security risk.
But i did try anyway to crack it while i was at school, and i couldn't get anywhere.
Can anyone tell me why this is an error, and how i could crack it (so i can learn to defend from it).
 Smoke me a kipper, ill be back for breakfast.
Smoke me a kipper, ill be back for breakfast.
MMORPG -- Many Men Online Role Playing as Girls
G.I.R.L -- Guy In Real Life
